0x09 Cross References [Reversing with Radare2]
This is a lecture from my 'Reverse Engineering with Radare2' course that is available here:
http://aetherlab.net/y/r2
You can check out my other courses here:
Website: http://aetherlab.net
Blog: / gergely.revay
Trainings:
Web Hacking: Become a Web Pentester - https://hackademy.aetherlab.net/p/web...
Learn Burp Suite, the Nr. 1 Web Hacking Tool - https://hackademy.aetherlab.net/p/bur...
Reverse Engineering with Radare2 - https://hackademy.aetherlab.net/p/rad...
Twitter: @geri_revay / geri_revay
Facebook: / aetherlab.net
===============================================
Transcript of the video:
===============================================
Hallo,
In this lecture we will continue towards our goal, we have to figure out how the password is checked. Of course from here it is not rocket science to find the next step, but for the sake of learning we will choose another approach. Let's look at the strings again and where it mentions passwords:
$iz~assword
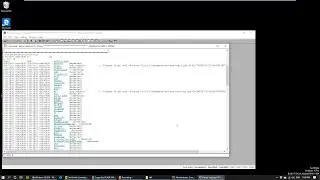
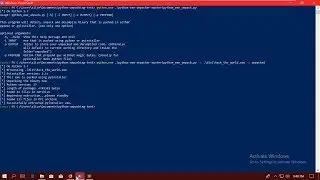
Looks interesting. There is the 'Password correct' string. What we want to do now is find out where it is used in the code. We can do that by checking the cross refernces to that address:
$ axt 0x0804940e
Another way is to seek to that address and print it:
$ s 0x0804940e
$ pd 10$$
This means print 10 bytes starting from here ($$). As you can see here are the strings and there is a comment to it telling you about the cross references. So what we found out is that the string is used in the function called 'check_password'. What a surprise. Let's check that out:
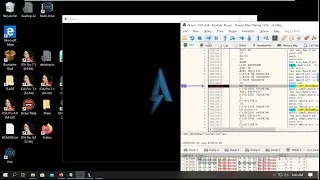
$ s sym.check_password
$ pdf
As you can see we can use here the same trick to find the password.
With that, it seems we reached our goal and found out the username and password. Let's try it out. It seems like the application is a password storage for Jabba. It seems that his chosen password revolve around a specific topic.
Anyway, even though we cracked the login, it does not seem to be any help for the rebellion, maybe if you want to look at Jabba's Tinder profile, which I do not recommend. You can see it but you cannot unsee it.








![[tool] Network Forensics with Tshark](https://images.mixrolikus.cc/video/BETB___XKs0)
![[Reversing Snippets] brbot Resource Load](https://images.mixrolikus.cc/video/pbnfLfPy9KE)
![[tool] Quick search for malware with DensityScout](https://images.mixrolikus.cc/video/vMu912jV6uc)
![0x0C - Cutter: FLARE-On #3 Challenge Part 1 [Reversing with Radare2]](https://images.mixrolikus.cc/video/hbEpVwD5rJI)
![0x0D - FLARE-On #3 Challenge Part 2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/QP9Cepdqf-o)
![0x09 Cross References [Reversing with Radare2]](https://images.mixrolikus.cc/video/yOtx6LL_R08)
![0x04 Target Application [Reversing with Radare2]](https://images.mixrolikus.cc/video/jlr3FablVIc)
![0x08 Navigation [Reversing with Radare2]](https://images.mixrolikus.cc/video/rkygJSjJbso)
![0x02 What is Radare2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/9fLfD2fZWiA)
![0x03 Environment Setup [Reversing with Radare2]](https://images.mixrolikus.cc/video/qGSFk_CkIaw)
![0x00 Intro [Reversing with Radare2]](https://images.mixrolikus.cc/video/Lva32dXS0mU)