Android Reversing: Flare Bear - Flare On 2019 Challenge 0x3
3rd challenge of the 2019 Flare On Reversing CTF. We are gonna reverse an android app to make a little bear ecstatically happy to give us the flag.
.Net Manipulation I mentioned in the video:
• Hacking the Memecat Battle Station - ...
Trainings:
Web Hacking: Become a Web Pentester - https://hackademy.aetherlab.net/p/web...
Learn Burp Suite, the Nr. 1 Web Hacking Tool - https://hackademy.aetherlab.net/p/bur...
Reverse Engineering with Radare2 - https://hackademy.aetherlab.net/p/rad...
Website: http://aetherlab.net
Twitter: @geri_revay
Blog: / gergely.revay
Transcript:
Hi! This is Geri and in this video we are gonna solve the third challenge of the flare on challenges 2019. This challenge is called flare bear. Before we get into it, first of all, the biggest lesson for me was to not overthink stuff too much. I intentionally left these tabs and all the open applications here just to give you a glimpse of how much stuff I worked on just so that I can realize at the end that you can solve the challenge on paper practically. But we will get there.
First what the challenge is about?
If you download flare bear and unpack it, you will get an APK file and message which says: we at flare created our own Tamagotchi pet: the flarebear: he is very fussy, keep him alive and happy and he will give you the flag.
APK files are Android applications so to run it, we will have to have some kind of emulator. I ended up trying multiple things: this is the official android studio emulator but it is actually not necessary. I mostly used a tool called: nox. Appearently there is a whole new market of android emulators for people who play with android games on pc. I didn't know it existed but it does and there is a bunch of emulators out there. Their advantage compared to android studio is, that it is much easier to use then installing the whole android studio. But anyway, let's see the game. So I right-click and do 'open with' and I will choose noxplayer. It starts up the emulator.
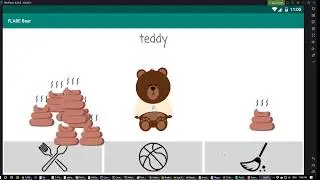
If we go back to homescreen you see there is a flare bear app and when it started you can choose a new flare bear, call your bear teddy and let's go!
We have this bear and we can do three things: feed it, play with it and at some point poops appear, which we can clean up. Let me poop a little bit. So now, we can clean up the poops. There is no poop.
That's all the game does. The first rabbit hole for me that I went down was that, as in the previous challenges I tried to do everything to manipulate this application into giving me the flag. If you haven’t seen that challenge you will find it in the description. You probably know that the android applications are mostly java code. The APK file can be unzipped or just opened with a tool. We can use the APK tool and then decompile it back to java so we can actually look at the java source code. That is pretty great and through an intermediate language called smully, or I think that's how its pronounced, you can manipulate the code as well, rebuild it back to an APK and run the manipulated code. But as I said this was a huge waste of time in this case. You can still try it though just for the sake of learning because that is the whole point of this CTF.
Now, let's look at the source code. We have the APK file and I have the APK tools installed.
There are a bunch of tools that we can use to decompile java code generally or android java code. The one I use is the jadx, because it has a nice gui. You can download it from the internet and just run the batchfile. Once running we open the flarebear.apk. As you can see it is pretty awesome, we have the source code for our android application. There is a main activity and there is a flarebear activity, credits and built config. If you remember there was a credits button in the main screen. However probably the interesting part of the application is the flarebear activity, because thats where everything happens when you have the flarebear on the screen.
At this point, we are just looking for something interesting that would lead us to the flag.
Here we can see all the functions in the flarebear activity and here is the code for the whole class. We can search for the string 'flag'. I check all these boxes. These are the android classes, they are not so interesting for us though. For us, it is interesting when it is in the com.fireeye. flarebear namespace. There is one and it is called dancewithflag. That sounds fun, so let's check it out.
... etc








![[tool] Network Forensics with Tshark](https://images.mixrolikus.cc/video/BETB___XKs0)
![[Reversing Snippets] brbot Resource Load](https://images.mixrolikus.cc/video/pbnfLfPy9KE)
![[tool] Quick search for malware with DensityScout](https://images.mixrolikus.cc/video/vMu912jV6uc)
![0x0C - Cutter: FLARE-On #3 Challenge Part 1 [Reversing with Radare2]](https://images.mixrolikus.cc/video/hbEpVwD5rJI)
![0x0D - FLARE-On #3 Challenge Part 2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/QP9Cepdqf-o)
![0x09 Cross References [Reversing with Radare2]](https://images.mixrolikus.cc/video/yOtx6LL_R08)
![0x04 Target Application [Reversing with Radare2]](https://images.mixrolikus.cc/video/jlr3FablVIc)
![0x08 Navigation [Reversing with Radare2]](https://images.mixrolikus.cc/video/rkygJSjJbso)
![0x02 What is Radare2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/9fLfD2fZWiA)
![0x03 Environment Setup [Reversing with Radare2]](https://images.mixrolikus.cc/video/qGSFk_CkIaw)
![0x00 Intro [Reversing with Radare2]](https://images.mixrolikus.cc/video/Lva32dXS0mU)