0x04 Target Application [Reversing with Radare2]
This is a lecture from my 'Reverse Engineering with Radare2' course that is available here:
http://aetherlab.net/y/r2
You can check out my other courses here:
Website: http://aetherlab.net
Blog: / gergely.revay
Trainings:
Web Hacking: Become a Web Pentester - https://hackademy.aetherlab.net/p/web...
Learn Burp Suite, the Nr. 1 Web Hacking Tool - https://hackademy.aetherlab.net/p/bur...
Reverse Engineering with Radare2 - https://hackademy.aetherlab.net/p/rad...
Twitter: @geri_revay / geri_revay
Facebook: / aetherlab.net
===============================================
Transcript of the video:
===============================================
Hi,
In this quick lecture I will introduce our target program for this course.
To play around with radare we will use an application, which was aquired in a very dangeouros covert operation and it was extracted fom an R3 maintenance droid. We will analyse the binary to find out whether it can be useful for the rebellion.
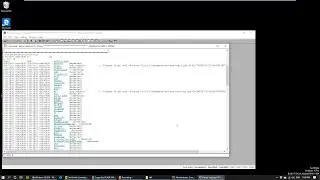
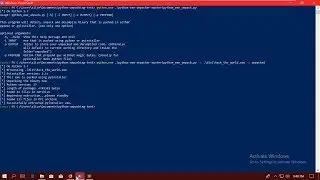
Let's try to execute the application.
$ ./server.exe
Let see if it opens a port:
$ netstat -apnt
As you can see it does. Let’s connect to it, maybe we find something out:
$ nc localhost 14884
It seems to be somekind of server with login. Let's try to login.
It doesn't work.
So our first reverse engineering goal can be to bypass the login and get access to the application.
So this is gonna be our target. In th next lecture we will start working with radare, first by reviewing the config.








![[tool] Network Forensics with Tshark](https://images.mixrolikus.cc/video/BETB___XKs0)
![[Reversing Snippets] brbot Resource Load](https://images.mixrolikus.cc/video/pbnfLfPy9KE)
![[tool] Quick search for malware with DensityScout](https://images.mixrolikus.cc/video/vMu912jV6uc)
![0x0C - Cutter: FLARE-On #3 Challenge Part 1 [Reversing with Radare2]](https://images.mixrolikus.cc/video/hbEpVwD5rJI)
![0x0D - FLARE-On #3 Challenge Part 2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/QP9Cepdqf-o)
![0x09 Cross References [Reversing with Radare2]](https://images.mixrolikus.cc/video/yOtx6LL_R08)
![0x04 Target Application [Reversing with Radare2]](https://images.mixrolikus.cc/video/jlr3FablVIc)
![0x08 Navigation [Reversing with Radare2]](https://images.mixrolikus.cc/video/rkygJSjJbso)
![0x02 What is Radare2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/9fLfD2fZWiA)
![0x03 Environment Setup [Reversing with Radare2]](https://images.mixrolikus.cc/video/qGSFk_CkIaw)
![0x00 Intro [Reversing with Radare2]](https://images.mixrolikus.cc/video/Lva32dXS0mU)