0x08 Navigation [Reversing with Radare2]
This is a lecture from my 'Reverse Engineering with Radare2' course that is available here:
http://aetherlab.net/y/r2
You can check out my other courses here:
Website: http://aetherlab.net
Blog: / gergely.revay
Trainings:
Web Hacking: Become a Web Pentester - https://hackademy.aetherlab.net/p/web...
Learn Burp Suite, the Nr. 1 Web Hacking Tool - https://hackademy.aetherlab.net/p/bur...
Reverse Engineering with Radare2 - https://hackademy.aetherlab.net/p/rad...
Twitter: @geri_revay / geri_revay
Facebook: / aetherlab.net
===============================================
Transcript of the video:
===============================================
Hi,
In this lecture I am gonna show you how you can navigate around in the binary with radare.
Even if we cannot execute the binary, from the info we learnt a lot. We found out that the application idoes something on the network, that there is somekind of login, and there are no binary protections in place. As we said our first target can be the login mechanism. Let's start reversing the program. When you start the radare you will be put to the entry point of the app.
$ r2 server.exe
Let's do the analysis.
$ aaa
Just to get thigs strait. The server.exe is not running right now. We are just disassembling the program and not executing it.
To go the main, we can do
$ s sym.main
The sym.main is just a reference created by radare to the address of the main function.
In case of main we can also do:
$ s main
As you can see the address where we stand has changed because we are standing now at the beginning of the main function.
Let's look at the list of functions:
$ afl
There is a function called 'authenticate', that could be interesting:
$ s sym.authenticate
What do you think is the command to see the dissassembled code?
P for print under that d for disassembly and f for functions.
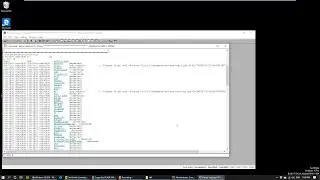
$ pdf
Which stands for 'print dissassemble function'. This show the assembly code of the function where we are standing. We can also say things like:
$ pdf @sym.authenticate
The @ literally means 'at' in radare. It can be followed by an address, register containing an address or a symbol like what we used. This is useful, because you don't have to change your position in the code to check out other parts of the code.
What you can see in this function is that after some string length calls the 'check_username' function is called. So let's go there:
$ s sym.check_username; pdf
If you look around, there are some logging built in, reading username, and then an interesting function is called, the 'compare_username'. Its parameters could be interesting. It is called with two local variables. And if you look closer one of them is initialized here:
0x08048af7 c785e4fbffff. mov dword [ebp - local_41ch], 0x6262616a
0x08048b01 66c785e8fbff. mov word [ebp - local_418h], 0x61
Let's see what is the value that is used in these variable. Just to prove again that the ? Is the most valuable command, you can do calculations with the '?' as well, in this case simply:
$ ? 0x6262616a
Or with the next line together:
? 0x616262616a
That looks really good. I can test quickly whether that works. Ohh yeah, so the username is jabba. Now we only need the password. Which we will see in the next lecture.
You can also do things like:
$ ? 0x10 + 6
In IDA you would add comments to the code to not forget things you have already found out about the code. You can do this in radare as well:
$ s 0x08048af7
$ CC username=jabba
In this lecture we have seen how the seek command works and how you can move around in the binary. Try to look at other interesting functions. After that join me in the next lecture.








![[tool] Network Forensics with Tshark](https://images.mixrolikus.cc/video/BETB___XKs0)
![[Reversing Snippets] brbot Resource Load](https://images.mixrolikus.cc/video/pbnfLfPy9KE)
![[tool] Quick search for malware with DensityScout](https://images.mixrolikus.cc/video/vMu912jV6uc)
![0x0C - Cutter: FLARE-On #3 Challenge Part 1 [Reversing with Radare2]](https://images.mixrolikus.cc/video/hbEpVwD5rJI)
![0x0D - FLARE-On #3 Challenge Part 2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/QP9Cepdqf-o)
![0x09 Cross References [Reversing with Radare2]](https://images.mixrolikus.cc/video/yOtx6LL_R08)
![0x04 Target Application [Reversing with Radare2]](https://images.mixrolikus.cc/video/jlr3FablVIc)
![0x08 Navigation [Reversing with Radare2]](https://images.mixrolikus.cc/video/rkygJSjJbso)
![0x02 What is Radare2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/9fLfD2fZWiA)
![0x03 Environment Setup [Reversing with Radare2]](https://images.mixrolikus.cc/video/qGSFk_CkIaw)
![0x00 Intro [Reversing with Radare2]](https://images.mixrolikus.cc/video/Lva32dXS0mU)