Finding Files Accessed by a Process
Website: http://aetherlab.net
Blog: / gergely.revay
Trainings:
Web Hacking: Become a Web Pentester - https://hackademy.aetherlab.net/p/web...
Learn Burp Suite, the Nr. 1 Web Hacking Tool - https://hackademy.aetherlab.net/p/bur...
Reverse Engineering with Radare2 - https://hackademy.aetherlab.net/p/rad...
-------------------------------------------------------------------------
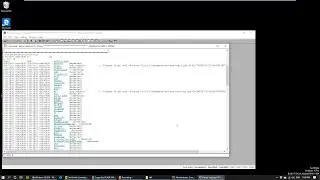
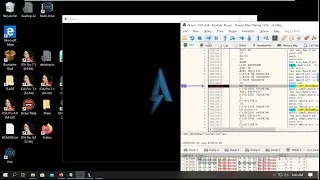
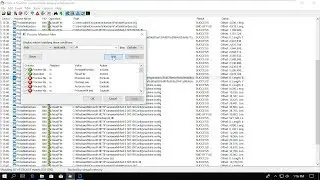
In this video we will look into how we can find out what files a specific process interacts with. For that I we will use the Process Mornitor tool from the Sysinternals Suite.
There are lots of different use cases why you would want to know files a process works with. For instance, in my case I was doing a security assessment of a desktop application. I knew that it stores data locally, so I wanted to find where that data is stored on the disk to be able to analyse whether it is stored securely (spoiler alert, it wasn't). But you could use the same method to analyse what a where a malware dropper stores the extracted or downloaded payload on the disk, to analyse that further.








![[tool] Network Forensics with Tshark](https://images.mixrolikus.cc/video/BETB___XKs0)
![[Reversing Snippets] brbot Resource Load](https://images.mixrolikus.cc/video/pbnfLfPy9KE)
![[tool] Quick search for malware with DensityScout](https://images.mixrolikus.cc/video/vMu912jV6uc)
![0x0C - Cutter: FLARE-On #3 Challenge Part 1 [Reversing with Radare2]](https://images.mixrolikus.cc/video/hbEpVwD5rJI)
![0x0D - FLARE-On #3 Challenge Part 2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/QP9Cepdqf-o)
![0x09 Cross References [Reversing with Radare2]](https://images.mixrolikus.cc/video/yOtx6LL_R08)
![0x04 Target Application [Reversing with Radare2]](https://images.mixrolikus.cc/video/jlr3FablVIc)
![0x08 Navigation [Reversing with Radare2]](https://images.mixrolikus.cc/video/rkygJSjJbso)
![0x02 What is Radare2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/9fLfD2fZWiA)
![0x03 Environment Setup [Reversing with Radare2]](https://images.mixrolikus.cc/video/qGSFk_CkIaw)
![0x00 Intro [Reversing with Radare2]](https://images.mixrolikus.cc/video/Lva32dXS0mU)