Learn Burp Suite, the Nr. 1 Web Hacking Tool - 02 - General Concept
Full training is available for free at:
http://hackademy.aetherlab.net
In this lecture we will cover the general concept of the Burp Proxy. I will explain how the test architecture works and we will discuss the basics of the Burp Suite.
Website: http://aetherlab.net
Blog: / gergely.revay
Trainings:
Web Hacking: Become a Web Pentester - https://hackademy.aetherlab.net/p/web...
Learn Burp Suite, the Nr. 1 Web Hacking Tool - https://hackademy.aetherlab.net/p/bur...
Reverse Engineering with Radare2 - https://hackademy.aetherlab.net/p/rad...
Video Transcript:
Now we have everything ready to work, but before we start, I would like to talk a little bit about the general concept of the Burp proxy. Burp is an intercept HTTP proxy which means that it works as a normal HTTP proxy and allows you to intercept and manipulate all requests and responses going through these proxies. It only works with the HTTP protocol Dow [sp] but now there’s even Ridge Clans [sp] use HTTP for communications. So this doesn’t mean that you can only test web applications with Burp. Also, if you work with SSL, Burp Upwards [sp] SSL so testing HTTP applications shouldn’t be a problem.
Let me show you this really sophisticated diagram. As you can see, we have these three things in our architecture. On the client side, we have our browser. On the server side, in our case, there will be the WebGoat. And all traffic goes through Burp, which is our proxy. It’s all simple. There is not much to say about this. It is that simple. In the previous section, we told the browser which proxy Burp Suite to send every traffic through Burp, and this is the most comfortable way. Sometimes you don’t have the luxury to do it this way because, for instance, only intertexting [sp] is supporting or proxying is not supported at all and you have to trick your operating system to send traffic through Burp. But this is the most comfortable setup so I recommend you to do it this way with FoxyProxy and directing everything to Burp as long as there’s no technical difficulty stopping you.
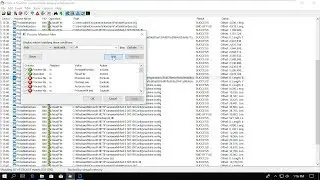
Let’s look at Burp a little bit before going into details. So this is our Burp proxy. Yeah, this is the Burp Suite. Burp consists of different modules. The modules that you see here, these tabs are the different modules – Target, Proxy, Spider, Scanner, et cetera. All these modules implement different features so they’re like different tools. And the whole concept is that if you find the request somewhere, then you can just take that request and just send it to the module where you can do what you want with that request. So, for instance, mostly our requests are here in Proxy because here you can see everything which you want through your proxy. And here we see that there was this request which was loading the WebGoat/attack page. So if we thought that this request was interesting and you want to play with it manually, then you can just right-click on it and say Send to the Repeater. And now you see the Repeater turned orange showing that there’s a new request there and you see here the request which was sent to the Repeater. Then you can start playing with this request and this Repeater. I don’t want to show you exactly what Repeater does because there will be a section for each module, and I will explain everything in details there.
Just to quickly go through, as I mentioned, Proxy is the place where you see what went through your proxy. The Target is the place where you see all traffic organized in a tree format. It’s good to have an overview of the application. And third is Spider. It’s a spidering tool. There’s a scanner which is not available in the free edition, but otherwise it’s an automated scanner tool. The Intruder is like the half-automated solution of testing where you can say what parts of the request you want to send and you want to see which payloads [sp] you want to use and then it will automate this. The Repeater is the varied manual test where you play with one request at a time and see what’s the response.
The Sequencer is good for testing randomness. It’s usually to test random tokens like session cookies, et cetera. It has some multiple [sp] tests built in which can find out the entropy [sp] randomness. The Decoder is a really simple tool to make your life easy to encode or decode URL code and HTML code, things like that. The Comparer allows you to compare requests, responses, generally some kind of strings. And you might know already but Burp is an extendable tool so you can write your own Burp extension and install that into Burp Suite and this way you can build in any plugs-ins that you want. And Options, Alerts, they’re not that interesting.
So these are the different modules of the tool. And now we’re going to start to go into details and talk about each module separately. So let’s go!








![[tool] Network Forensics with Tshark](https://images.mixrolikus.cc/video/BETB___XKs0)
![[Reversing Snippets] brbot Resource Load](https://images.mixrolikus.cc/video/pbnfLfPy9KE)
![[tool] Quick search for malware with DensityScout](https://images.mixrolikus.cc/video/vMu912jV6uc)
![0x0C - Cutter: FLARE-On #3 Challenge Part 1 [Reversing with Radare2]](https://images.mixrolikus.cc/video/hbEpVwD5rJI)
![0x0D - FLARE-On #3 Challenge Part 2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/QP9Cepdqf-o)
![0x09 Cross References [Reversing with Radare2]](https://images.mixrolikus.cc/video/yOtx6LL_R08)
![0x04 Target Application [Reversing with Radare2]](https://images.mixrolikus.cc/video/jlr3FablVIc)
![0x08 Navigation [Reversing with Radare2]](https://images.mixrolikus.cc/video/rkygJSjJbso)
![0x02 What is Radare2 [Reversing with Radare2]](https://images.mixrolikus.cc/video/9fLfD2fZWiA)
![0x03 Environment Setup [Reversing with Radare2]](https://images.mixrolikus.cc/video/qGSFk_CkIaw)
![0x00 Intro [Reversing with Radare2]](https://images.mixrolikus.cc/video/Lva32dXS0mU)