CISSP Series Domain3 Episode 3 - Threat Modeling
CISSP Series Domain3 Episode 3 - Threat Modeling
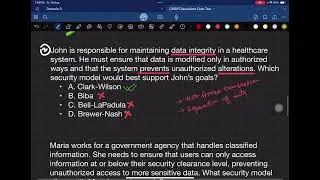
Welcome back, friends! Welcome to the concepts of CISSP. In this video, we'll be discussing threat modeling. Threat modeling is a topic best suited for discussing risk assessment, and I covered it in Domain 1. In that domain, we delved deep into risk, how to identify it, and how to manage it within an enterprise. We discussed concepts like NIST 830, NIST 839, and 853A for assessment and related concepts.
If you want more details on overall risk management, please refer to my video in Domain 1's risk management discussion. We also covered key definitions necessary to understand NIST documentation and the CISSP syllabus, including vulnerability, threat, risk, asset value, and exposure factor. Knowing these terms in advance will help you understand further details in Domain 3, which covers security architecture and engineering.
Now, let's dive into what threat modeling means for an organization. Threat modeling is a security process, specifically part of enterprise risk management. It involves identifying, categorizing, and analyzing threats. The primary goal of threat modeling is to prioritize potential threats against valuable assets, emphasizing the concept of asset-threat pairing.
There are common approaches to threat modeling, which can be proactive or reactive, often a mix of both. Proactive threat modeling occurs during product design, software development, or while creating security policies. Reactive threat modeling, or threat hunting, happens after product deployment and focuses on finding vulnerabilities.
Mixed threat modeling combines proactive and reactive approaches, typically because it's impossible to identify all threats during initial design or policy development. Organizations may use both approaches, involving different teams and techniques.
Reactive threat modeling, or threat hunting, often involves ethical hacking, penetration testing, source code reviews, and fuzz testing. It may lead to the release of patches for software products, a practice known as patch management.
Understanding the common approaches to threat modeling is essential, as most organizations use a combination of proactive and reactive methods. These approaches ensure a comprehensive security program.
Next, let's explore the common approaches to threat identification, which fall into three major categories: asset-focused, attacker-focused, and software-focused.
Asset-focused threat identification is based on asset valuation and asset-threat pairing, also known as vulnerability-threat pairing. The presence of vulnerabilities in assets makes them susceptible to threats, creating a pairing.
Attacker-focused threat identification involves identifying attackers' motives, goals, tactics, techniques, and procedures (TTPs). A notable example is the STRIDE model, which categorizes threats as Spoofing, Tampering, Reputation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege.
Software-focused threat identification, often used during software development, follows secure design principles. One example is Microsoft's SDL (Secure Development Lifecycle), which encompasses secure design, default security settings, secure deployment, and secure communication.
In conclusion, threat modeling is a crucial aspect of CISSP, and understanding these concepts will help you excel in your preparation for the exam. Remember to review the specific models and methodologies mentioned in this video to solidify your knowledge. Best of luck with your CISSP exams!
🔔 Follow new updates on https://cisspmadeeasy.com/