CISSP Series Domain3 Episode 27 - Man-in-the-middle Attack MITM
Mastering CISSP: The Art of Symmetric Key Cryptography with Karan Arjun
Hello friends, welcome back! It’s time for the 27th episode of our thrilling series, "Concepts of CISSP". Buckle up, as we dive deep into the world of cryptography, focusing on symmetric key cryptography in Domain 3: Security Architecture and Engineering.
What We’ve Covered So Far
We’ve discussed the basics: what cryptography, cryptology, and cryptanalysis are. Now, let's zoom in on symmetric key cryptography. Imagine a world where one key rules them all—for both encryption and decryption. This magic key is known as a symmetric key.
The Nostalgic Example: Karan Arjun
To spice things up and add a bit of Bollywood flavor, let’s revisit the movie Karan Arjun. Released back when I was in class 9, this film features Shah Rukh Khan and Salman Khan as the titular characters. Picture this: Karan wants to send a secret message to Arjun. They need a session key to ensure their communication is secure.
But here’s the catch—Karan and Arjun are miles apart. They can't just meet up to exchange the key. If they could, they might as well exchange the message in person, right? There could be a scenario where they exchange the session key beforehand and use it in times of need or danger.
In the world of computer network security, we need a universal solution, applicable at all times. Enter the Diffie-Hellman key exchange—a mathematical marvel that saves the day.
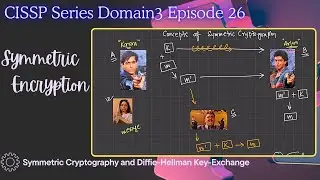
Diffie-Hellman Key Exchange Explained
In our previous episode, we explored the Diffie-Hellman key exchange using Karan and Arjun. If you missed it, click • CISSP Series Domain3 Episode 26 - Symmetri... to catch up. This algorithm allows two parties to share a secret key over an unsecure channel.
Here's the simplified version:
1. Share two numbers, N and G: These numbers are publicly exchanged. Let’s say N is 11 and G is 7.
2. Pick two secret numbers, X and Y: Karan picks X = 3, and Arjun picks Y = 9.
3. Calculate A and B: Using the formula \(A = G^X \mod N\) and \(B = G^Y \mod N\), Karan calculates A = 2 and Arjun calculates B = 8.
These numbers, N, G, A, and B, are exchanged over the unsecure channel. Both Karan and Arjun then use these to compute the same secret key, ensuring secure communication.
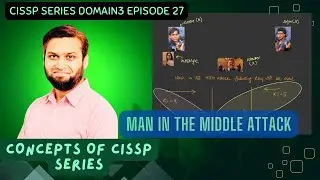
The Villain: Man-in-the-Middle Attack
But every hero story has a villain. Enter the man-in-the-middle attack, also known as the Bucket Brigade attack. Imagine the evil Amrish Puri (the quintessential Bollywood villain) intercepting Karan and Arjun's communication.
Here’s how it unfolds:
1. Interception: Amrish intercepts the values A and B.
2. Manipulation: He sends his own values to Karan and Arjun, deceiving them into thinking they’re communicating with each other.
Karan calculates his key, Arjun calculates his, but both are actually communicating through Amrish, who now has the keys to both conversations. He can read, modify, and manipulate the messages at will.
The Solution: Combining Asymmetric and Symmetric Keys
So, is Diffie-Hellman useless? Not at all! We can still use symmetric key encryption for its speed and efficiency. For key exchange, we use asymmetric encryption (which we’ll cover in the next episode).
By combining the best of both worlds, we exchange keys securely using asymmetric encryption (public and private keys) and then encrypt data using the fast and efficient symmetric key encryption.
Wrapping Up
And that, my friends, is a glimpse into the fascinating world of symmetric key cryptography and key exchange. If you enjoyed this post, give it a thumbs up, share it with friends preparing for the CISSP exam, and subscribe for more engaging content. I hope this helps you pass the CISSP exam with flying colors and ace those practice questions.
Stay curious, keep learning, and remember, even cryptography can be fun—especially with a little Bollywood twist!
Thank you and see you next time!