CISSP Series Domain3 Episode 23 - Security building blocks of an Information System
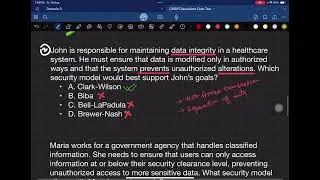
In this video, I delve into the concepts of #CISSP, specifically focusing on the security capabilities of information systems. We explore security building blocks or Security Primitives, such as memory protection, virtualization, and secure crypto processors. Memory protection involves techniques like CPU dual mode operation and Address Space Layout Randomization (ASLR) to prevent unauthorized access to memory. I also touch upon vulnerabilities like Spectre and Meltdown.
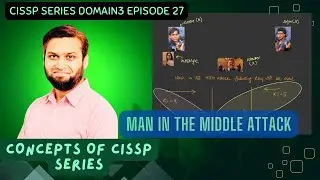
Moving on to virtualization, I explain the two types of hypervisors (type one and type two) and associated vulnerabilities like hypervisor escape, resource exhaustion, double attack surface, and guest-to-guest attack. Lastly, I discuss secure crypto processors like secure enclaves, TPM, cryptographic modules, HSMs, and smart cards. Each has its use cases and associated risks, emphasizing the importance of understanding these components for a comprehensive grasp of CISSP concepts.
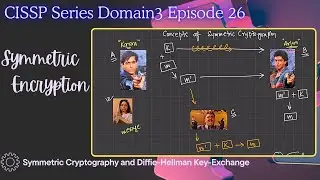
Join me in the next video as we dive into cryptography, starting with Symmetric cryptography and exploring the fascinating world of Asymmetric cryptography and public key infrastructure. Thank you for watching!