CISSP Series Domain3 Episode 21 - Bell La Padula, Biba, Clak-Wilson and Brewer Nash Model
CISSP Series Domain3 Episode 21 - Bell La Padula, Biba, Clak-Wilson and Brewer Nash Model
00:00 Introduction and BLP
09:12 Biba Integrity Model
14:47 Clark Wilson Model
19:33 Brewer Nash Model
In this video, I'm discussing four important security models: Bell La Padula (BLP), Biba Integrity Model, Clark Wilson Model, and Brewer Nash Model. Understanding these models is crucial for passing the CISSP exam.
1. *Bell La Padula (BLP) Model:*
BLP is all about maintaining confidentiality.
It has three main rules: Simple Security Property, Star Property, and Discretionary Security Property.
Simple Security Property: Users can't read data at a higher security level.
Star Property: Users can't write data to a lower security level.
Discretionary Security Property: This property is all about access control and complements the first two.
2. *Biba Integrity Model:*
Biba focuses on data integrity.
It's based on two axioms: Simple Integrity Axiom and Star Integrity Axiom.
Simple Integrity Axiom: Users can't read down to lower integrity levels but can read at or above their level.
Star Integrity Axiom: Users can't write up to higher integrity levels but can write at or below their level.
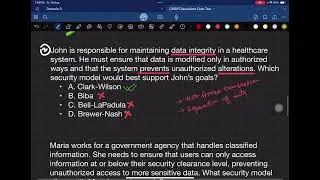
3. *Clark Wilson Model:*
Clark Wilson also aims to maintain data integrity.
It's based on two fundamental concepts: Well Formed Transactions and Separation of Duties.
Well Formed Transactions ensure that data entries are accurate by not allowing erasing but instead making corrective entries.
Separation of Duties ensures that users have specific, limited rights to access data, preventing errors and manipulation.
4. *Brewer Nash Model (Chinese Wall Model):*
This model is all about preventing conflicts of interest.
It follows the principle of Segregation of Duties, where a user's access to data is restricted based on what they are already allowed to access.
Objects, Company Data Sets, and Conflict of Interest Classes are used to implement this model.
These models have distinct objectives and principles, and they are critical for CISSP exam preparation. Understanding them will be invaluable when answering CISSP objective questions.