Bob Vulnhub Walkthrough - Getting Inside - [Part 1]
Burp Suite Deep Dive course: https://bit.ly/burpforpros
________________________________________________________________________________________________ Recon in Cybersecurity course: https://bit.ly/cybersecrecon
Python Basics course: http://bit.ly/37cmhlx
Python for Pentesters course: http://bit.ly/2I0sRkm
Join me and other cyber-geeks on discord: http://bit.ly/2KH6aST
Join my SQUAD (for discounts'n'stuff): http://bit.ly/2xhSvM2
Hire me as a penetration tester: https://dgtsec.com/penetration-testin...
101 Pentesting Training: https://dgtsec.com/cybersec-pentestin...
101 Cybersecurity Consulting: https://dgtsec.com/cybersec-pentestin...
Connect with me:
Help me continue creating videos: https://www.buymeacoffee.com/cristivlad
Linkedin: / cristivlad
Twitter: / cristivlad25
Facebook page: / cristivladz
Facebook group: / cybersecpros
Hackthebox: https://www.hackthebox.eu/profile/27034
Tryhackme: https://tryhackme.com/p/cristi
Peerlyst: https://www.peerlyst.com/users/cristi...
Discord: https://disboard.org/server/608756357...
Books I recommend for Penetration Testing and Ethical Hacking:
1. TJ O'Connor - Violent Python: https://amzn.to/31vH2GB
2. Dafydd Stuttard - Web App Hacker' s Handbook (2nd Ed): https://amzn.to/2MRcjk3
3. Peter Yaworski - Web Hacking 101: https://amzn.to/2KTvJSy
4. Jon Erickson - Hacking: The Art of Exploitation (2nd Ed):
https://amzn.to/2WHr3BD
5. Peter Kim - The Hacker Playbook 3 (2018): https://amzn.to/2MQiTXK
6. Peter Yaworski - Real-World Bug Hunting: https://amzn.to/37GB87K
It helps me tremendously if you support these educational videos:
/ cristivlad
My course Developing Ethical Hacking Tools with Python on Cybrary: http://bit.ly/2J5USbC
If you're a Youtuber, how can you survive without TubeBuddy? http://bit.ly/37dgFYr
Learn hands-on pentesting (free trial): http://bit.ly/2LzKrPJ
Hacker Wearables: http://bit.ly/2IDAQEo
Short-clips via: https://mixkit.co/
__________
Whatever type of tests you're doing, only perform them in safe and legal environments and with the appropriate permissions.
__________
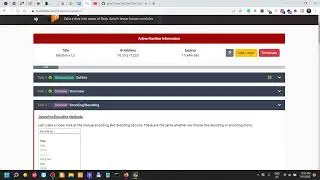
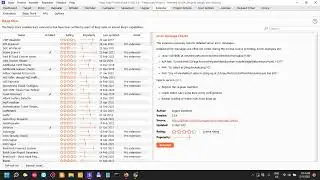
Bob is a vulnerable machine from vulnhub. It runs a web server and on a superficial look it only has port 80 open. On a closer inspection, we also find out it has port 25468 open, which is an ssh server. The vector for getting inside the server was pretty simple, very simple to say the least. That's what we look into in this video.
If you want to see more of these cybersecurity related videos, please hit the like button and leave a comment below.
Only perform these types of engagements in safe and legal environments and with the appropriate permissions. This video is for educational purposes only.







![How I Hack or Pentest Mobile Apps [feat @BugBountyReportsExplained]](https://images.mixrolikus.cc/video/tMMFx1JzEek)
![My Favorite Burp Suite Extensions and How I use Them [feat @BugBountyReportsExplained]](https://images.mixrolikus.cc/video/P-8Qg5GkbbI)
![The Most Common Vulns I Find in Pentests [feat. @BugBountyReportsExplained]](https://images.mixrolikus.cc/video/iBQJ7iSW0vQ)






![Google Bard vs. GPT4 - Hands-On First Look [Cybersecurity]](https://images.mixrolikus.cc/video/xhZ-rueqllg)



