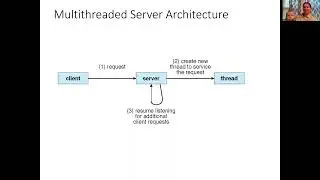
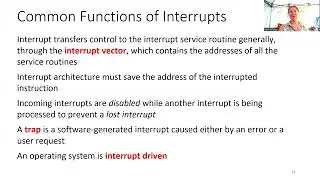
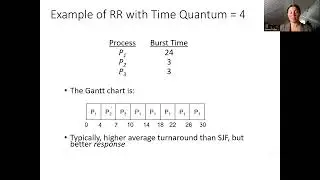
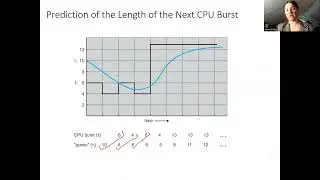
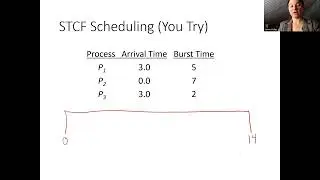
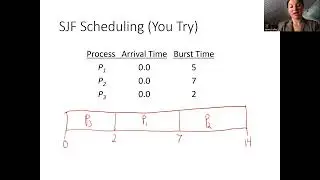
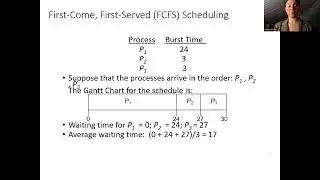
Computer Systems Bomblab Phase 4 Walkthrough
In this video, I demonstrate how to solve the Bomblab Phase 4 for Computer Systems. I assume that the student has already logged into a Linux environment that will run the bomb.
1. Navigate to where your bomb is.
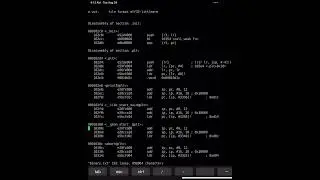
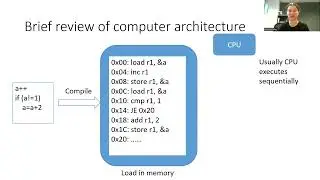
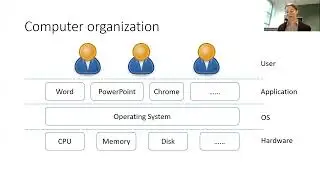
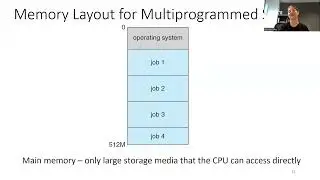
2. Chunk phase_4 into portions of assembly code that represent logical chunks, and then determine how our input interacts with those chunks. One of our inputs has some comparisons made to it which will help us later.
3. Phase_4 calls a function named func4. Examine func4 for recursive calls, blocking out base cases first.
4. Try out a guess for phase_4 with 2 requested arguments using gdb. Don't worry, it won't be correct--but it will help you walk through the code execution and see into memory. It will also help to identify which argument is kept in which order in the stack.
5. If your data will cause an explosion, modify it and rerun to get to this point, then set a break point for just after func4 returns. The outcome of this function is compared to another of our inputs, which should help us defuse the phase.
6. Restart the bomb using "run" again, and this time put in the inputs you think are correct. Did it work?
Good luck!




![CORRUPTION TIME [0.6.0] [Incutia] باللغة العربية PT ESPAÑOL ANDROID Y PC](https://images.mixrolikus.cc/video/fgo4c0crog0)