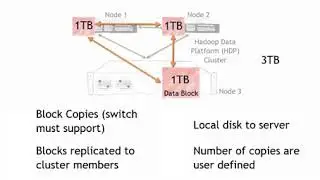
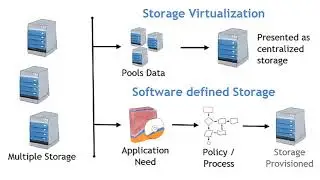
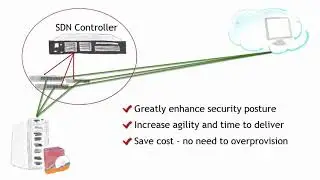
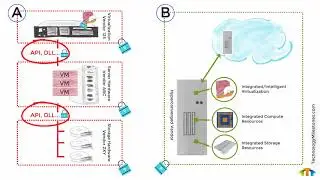
Converged for Security. The differences between legacy and converged infrastructure
Cyber activities, creation of controls and policies, and ultimately securing the environment is greatly simplified when you reduce the number of variables within the environment. The images on the left side of the illustration (A) represent a legacy environment. In contrast, the images on the right side of the diagram (B) represent a converged (CI) / hyper-converged (HCI) environment. The locks represent the complexity of developing cyber controls, policies, and baselines to maintain a healthy cyber posture. (See the blog post at https://www.technologymilestones.com/...)
One of the challenges in the legacy environment, as illustrated (A), is that the virtualization, server, and storage vendors are all different. As a result, they must use "connectivity" (APIs, DLLs) to communicate with one another, which creates additional performance, compatibility, configuration, and security challenges. The objective of a healthy cyber posture is to reduce the number of variables and threat vectors.
The reason why many organizations are moving away from legacy infrastructure to converged infrastructure is to reduce the complexity and security vulnerabilities inherent in legacy infrastructure. Converged infrastructure is most potent when the same vendor provides all of the resources, to include virtualization, compute, and storage.
At the root of compliance to regulatory requirements or the establishment of the security foundation to protect organizational assets, is the security boundary. The security boundary establishes a level of protection from unknown variables, consider it the "moat" that exists around the castle. With legacy infrastructure (A), the security boundary includes multiple sub boundaries that exist between each vendor that is providing virtualization, server hardware, and software. The APIs and DLLs or connectivity between the vendor solutions is a concern that is addressed by specific security controls as well. The security boundary of a legacy infrastructure includes all of the sub boundaries and controls needed to secure a multivendor infrastructure. It is not difficult to understand why organizations are quickly moving to converged technologies, as the management and security of legacy environments are considerably more complicated than a converged environment.
A converged environment simplifies the development of security controls; additionally, the management of the environment is optimal when provided by a single vendor. The vendor should also include a "bare-metal" alternative that can reside in public clouds, a natural extension of services and security boundary. Consistency and repeatability are two objectives favorable to a highly secure environment and converged technologies deliver. As you review converged technologies for your environment, consider the origin of the technologies within your converged solution. Remember, several of the world's largest hardware manufacturers have acquired technologies like virtualization and storage to augment their server hardware. If the manufacturer maintains an autonomous relationship with acquired technologies like virtualization and storage, consumers should understand if the converged technology is closer to a legacy infrastructure (A) into an actual converged infrastructure (B).







![Produce More - Examples and Benefits of Task Management [19124.856]](https://images.mixrolikus.cc/video/hAewYTnsEdE)
![EASY- Examples - ChatGPT as my Daily Assistant [18032023.908]](https://images.mixrolikus.cc/video/RBvVRmvDWJs)
![Remote Worker TIP - Use browser to separate work and personal [241222.19]](https://images.mixrolikus.cc/video/PCW6K_RYt-g)