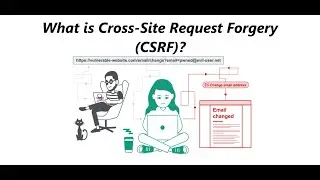
Exploiting server-side parameter pollution in a query string - Lab#04
In this video, I demonstrate how to exploit a server-side parameter pollution (SSPP) vulnerability in a query string to bypass access controls. By manipulating duplicate parameters, I gain access to the administrator account, and then proceed to delete the user carlos.
This lab shows how improperly handled query parameters on the server side can lead to privilege escalation and unauthorized actions.
🔹 Lab Type: Server-Side Parameter Pollution (SSPP)
🔹 Vulnerability: Insecure handling of duplicate query parameters
🔹 Attack Goal: Log in as administrator and delete carlos
🔹 Credentials for testing: wiener:peter
📌 Like & Subscribe for more web security lab walkthroughs and ethical hacking tutorials! 💻🛡️
#ServerSideParameterPollution #WebSecurity #BugBounty #EthicalHacking #PortSwigger #CyberSecurity #SSPP #AccessControlBypass


![李克勤版本的《晚风心里吹》哀而不伤 内敛深情 [精选中文好歌] | 中国音乐电视Music TV](https://images.mixrolikus.cc/video/Amd_N31T3pQ)