Unveiling Dex2C Compiled Android APKs || Reverse Engineering Dex2C || Recovering smali from native
!!ONLY FOR EDUCATIONAL PURPOSES!!
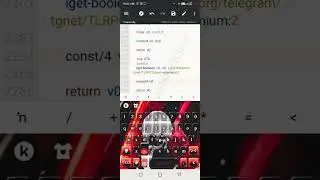
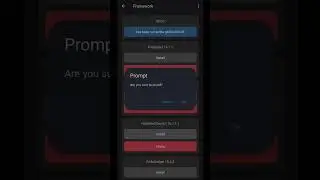
Ever wondered how to reverse engineer a Dex2C compiled Android APK? In this video, we delve into the intricate world of reverse engineering and show you how to extract SMALI codes from the native code of a Dex2C compiled program.
We start by explaining the main idea behind this reverse engineering process. Then, we demonstrate the use of powerful tools such as Radare2, Notepad++, MT Manager, and JEB Decompiler to successfully remove the native code and retrieve the original SMALI codes.
This video is a must-watch for anyone interested in understanding the inner workings of Dex2C and how to reverse engineer its compiled output. Whether you're a security professional, a developer, or just a tech enthusiast, this video will provide you with valuable insights and practical skills.
So, if you're ready to take your reverse engineering skills to the next level, sit back, and let's dive into the world of Dex2C compiled Android APKs!
radare2: https://radare.org/
Dex2C: https://github.com/codehasan/dex2c
JEB: https://www.pnfsoftware.com/jeb
MT Manager: https://mt2.cn/
Thanks,
Happy Reversing 😉
[Description Enhanced by Ai]
#reverseengineering #dex2c #smali #modding #dalvik #nativecode




![CORRUPTION TIME [0.6.0] [Incutia] باللغة العربية PT ESPAÑOL ANDROID Y PC](https://images.mixrolikus.cc/video/fgo4c0crog0)



![Dumping [file name ]cpp.so in android / il2cpp dumper in android 🙂 || ABHI - THE MODDER ||](https://images.mixrolikus.cc/video/7Vo942WZkP4)