Unleashing the Power of BlackMamba: The Ultimate C2 Post Exploitation Framework
Welcome to our YouTube video on "BlackMamba – C2 post exploitation Framework"! In this video, we dive deep into the incredible power and versatility of BlackMamba, the ultimate C2 post exploitation framework.
BlackMamba, a cutting-edge tool developed by our expert team at [Your Company Name], enables penetration testers and ethical hackers to efficiently carry out advanced post exploitation activities. With its extensive range of features and capabilities, BlackMamba has revolutionized the field of post exploitation and has become a go-to framework for security professionals worldwide.
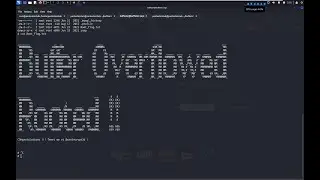
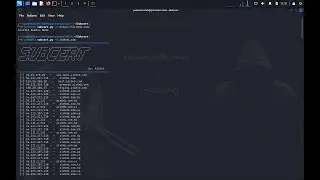
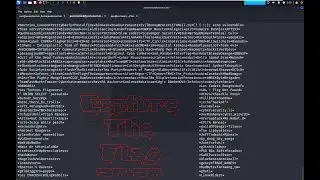
In this demonstration, we showcase the various modules and functionalities that make BlackMamba a force to be reckoned with. From stealthy C2 communications to advanced file management and system control, BlackMamba offers unparalleled control and agility in the post exploitation phase.
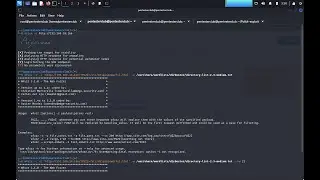
Our expert presenter will guide you through the installation process, provide an overview of the framework's architecture, and demonstrate real-world scenarios illustrating how BlackMamba can be utilized effectively. We cover everything from establishing a covert command and control channel to navigating networks undetected, ensuring you gain a comprehensive understanding of BlackMamba's potential.
Stay tuned as we explore the key features that set BlackMamba apart, including its flexibility, compatibility with various operating systems, and ability to evade detection by traditional security solutions. Applying advanced obfuscation techniques and encryption methods, BlackMamba maintains a low profile while delivering high impact.
Whether you are a seasoned professional or an aspiring ethical hacker, this video will equip you with the knowledge and skills required to leverage BlackMamba effectively in your security assessments. Discover the essential tactics, tips, and tricks to optimize your post exploitation tasks and take your cybersecurity skills to the next level.
Don't miss the opportunity to witness the true power of BlackMamba in action. Watch this video now and unlock the immense potential of this unparalleled C2 post exploitation framework!
~-~~-~~~-~~-~
Please watch: "Penetration Testing Jenkins Server"
• Penetration Testing Jenkins Server
~-~~-~~~-~~-~